PA Remote Access or GLOBAL PROTECT
- Mukesh Chanderia

- Jan 16, 2022
- 2 min read
Updated: Feb 27, 2022
GLOBAL PROTECT
There are three components
Global Protect Portal: : Can Have Multiple Gateway [Multiple Firewall to connect Main,DR]
Global Protect Gateway: : There can be multiple Firewalls [Main, DR]
Global Protect Client: : Must be downloaded and activated on PAFW
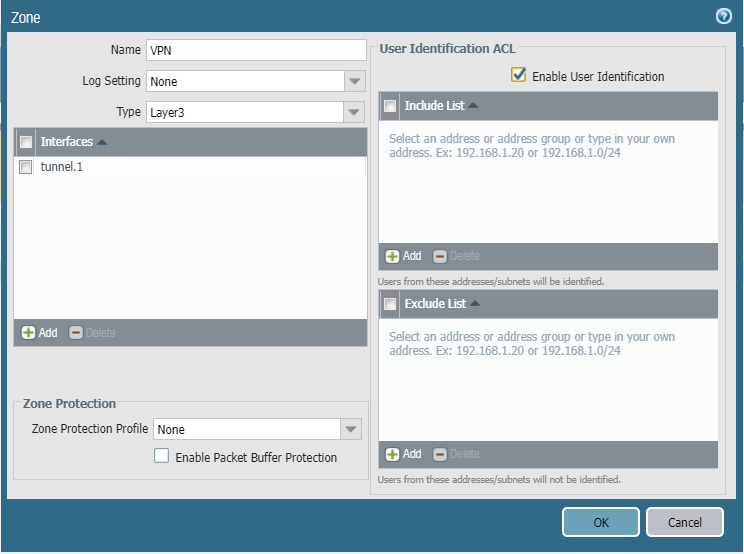
Step1: Create a New Zone e.g., GPZONE and enable "USER IDENTIFICATION"
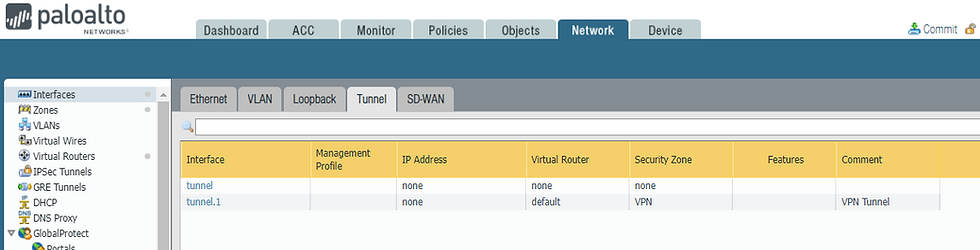
Step2: Create a Tunnel Interface and put it in GPZONE
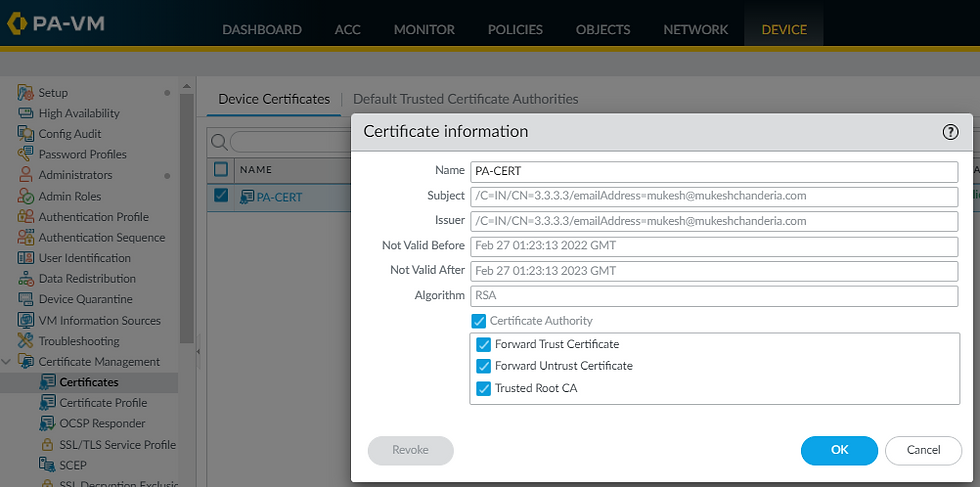
Step3: Generate self-signed digital certificate or install CA Certificate [both Root & Identity Certificate]
Common Name: Firewall External Interface IP address or FQDN [Fully Qualified Domain Name]
Step4: Create Authentication Profile and allow all users or specific Users/Groups
Step5: Create User from local user database or Use external User database [AD database]
Step6: Create Global Protect Gateway
Step7: Add Global Protect Portal
Interface: Outside Physical Interface
Authentication: Authentication Profile
TLS / SSL Profile: Create New Profile with self-signed digital certificate.
Step8: Create Security Policy
Step9: Commit
Step 1:
Download & activate a software of Global client in Firewall which you want to use.
Devices --> Global Protect Client

Step 2: Create New Tunnel Interface & also new Zone "VPN". No ip is required to be assigned to tunnel.
In Zone enable user Identification
Step 3: Device --> Certificate Management --> Certificates --> Generate

Step 4: Get Certificate Trusted
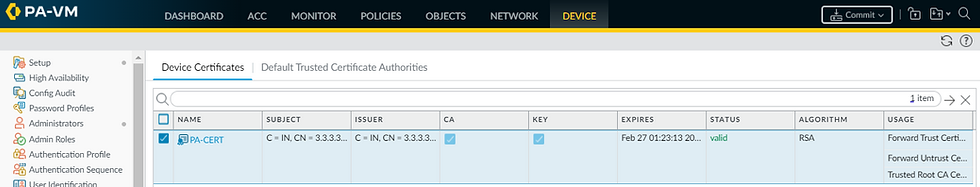
Step 5:
Create SSL/TLS Profile:
Device --> Certificate Management --> SSL/TLS Service Profile

Step 6: Create Local Users / or AD database can be used

Step 7: Create Authentication Profile to allow which user can access RAVPN.
We chose all users.


Multi Factor Authentication can also be enabled. You may see list of supported vendors.

Step 8: Create GP_GATEWAY
Network --> Gateway
This Gateway can either be external interface of Fw or ip from Public ip Pool.

To enforce client certificate authentication, select Certification Profile.


SSL Authentication is generally required to connect to Gateway & download certificate.

Add ip pool which will be assigned by firewall to client systems.

Add the subnet for which if traffic originates then only pass-through VPN tunnel.
This 192.168.204.0/24 is our internal subnet.

We are required to provide DNS server ip if we don't enable split tunnel. As then all traffic going to internet will to pass through firewall.

Step 9: Now do similar config for Portal
Network --> Global Protect --> Portal


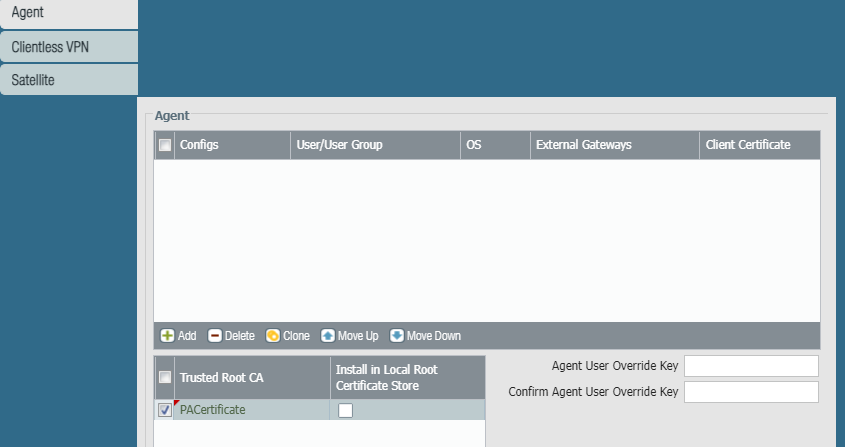
Under Agent we also need to specify certificate which will be installed on client.

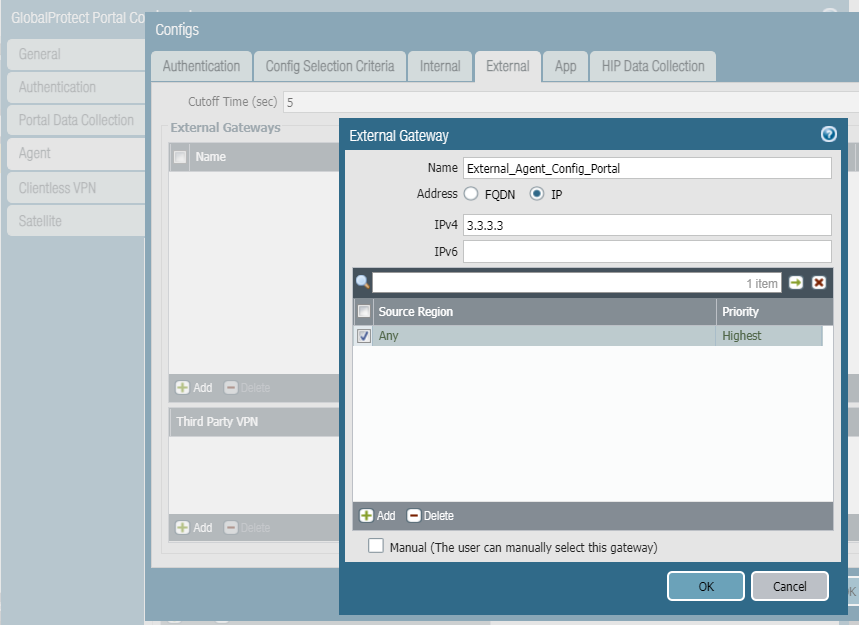
Define the ip as well as region from where user can connect.
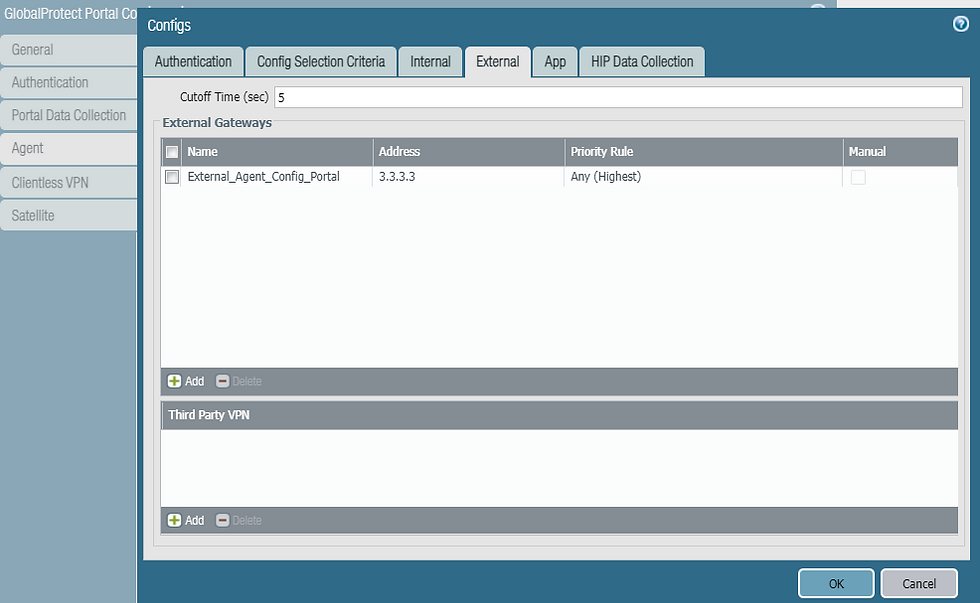
There is an option to add third party VPN for Cisco or Juniper

Step 10
Define Security Policy for VPN User

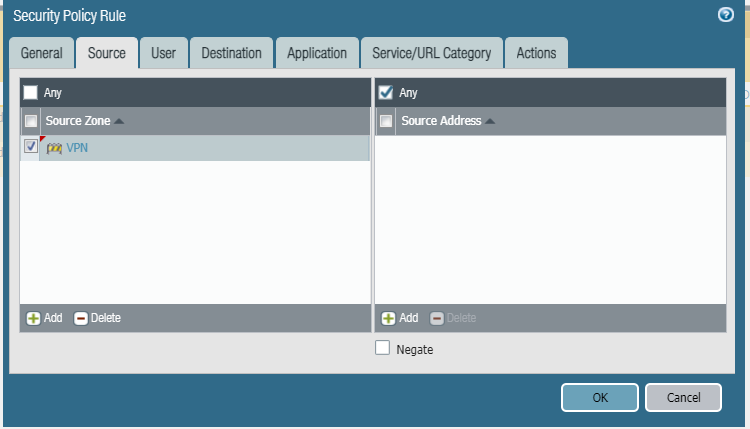


Security Policies to require to allow traffic i.e. from VPN Zone to DMZ or Inside.
Note: SSL ,panos-global-protect & panos-web-interface must be allowed in Application (in case any isn't selected)




Comments